Token Based Authentication using Asp.net Core Web Api
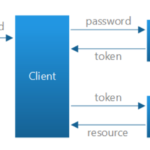
Using Token Based Authentication, clients are not dependent on a specific authentication mechanism. A token is generated by the server if the user is authenticated and send it back to the user.
So to acces a specific ressource, the client must include the generated token in the header of subsequent requests and the Web API Server have some APIs to understand, validate the token and perform the autorization
This approach provides Loose Coupling between client and the Web API.
In my previous tutorial Angular JS Token-based Authentication using Asp.net Identity and Asp.net web API I have build an authentication server using an oAuth Bearer Token.
In this tutorial, I will use JSON Web Token (JWT) , for more information about JWT please take a look at https://jwt.io/
JWT enable us to securely transfer data between server and client .
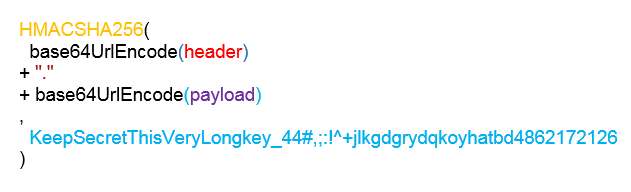
A JWT Token is composed of 3 parts base64 encoded separated by a dot(.) : a header, a payload and a signature : header.payload.signature
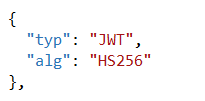
- Header : contains a Typ (should be JWT) and a Hashing algorithm HS256, RS512, ES356, etc…
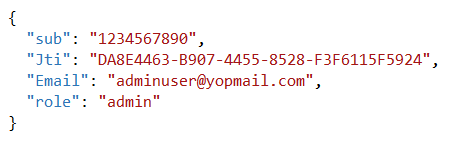
- Payload contains the information witch we need to transfer to client such as Claims related to the token
- Signature A Hash of Header and Payload using a secret Key
JWT therefore allows to exchange content for an authenticated user due to the secret key used in the signature. The signature also ensures the integrity of the content.
Even if every one can holds the token, he cannot tempored the payload due to the signature with the Secret Key.
SSL helps prevent against to MitM (man-in-the-middle) attacks.
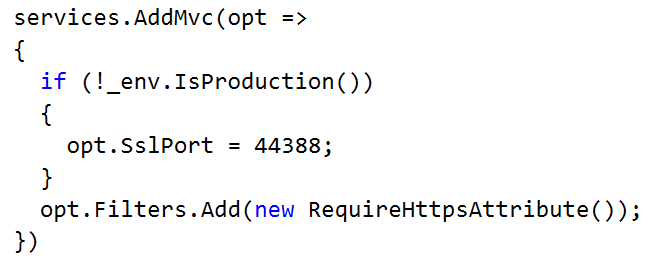
Securing our web application consists of two scenarios Authentication and Authorisation
- Authentication identifies the user. so the user must be registered before, using login and password or third party logins like Facebook, Twitter,
- Authorisation talks about Permission for authenticated users
– what is the user (authenticated) allowed to do ?
– What ressources can the user access ?
I’m going to build a Token-based Authentication Server using ASP.Net Core Identity , ASP.Net Core Web API and Entity Framework Core
So lets create a new ASP.NET Core Web Application Project
Dependencies
install this packages
install-package Microsoft.AspNetCore.Identity
install-package Microsoft.AspNetCore.Identity.EntityFrameworkCore
install-package Microsoft.EntityFrameworkCore.SqlServer
install-package Microsoft.EntityFrameworkCore.Tools
Setup Indentity database
Create a User model that inherits from IdentityUser and extend it with additional properties such as JoinDate, JobTitle and Contract.
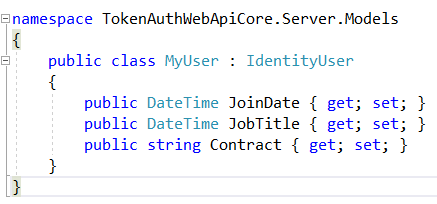
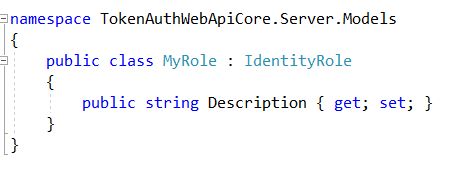
Create a Role model that inherits from IdentityRole and extend it with additional properties such as Role Description
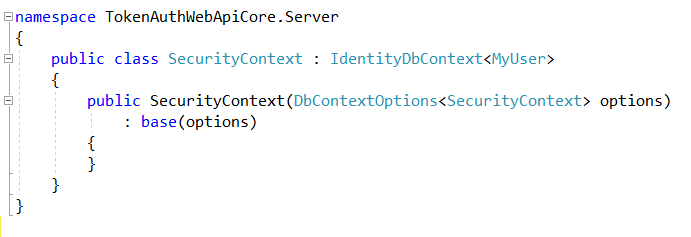
Create an IndentityContext that inherits from IdentityDbContext<MyUser>
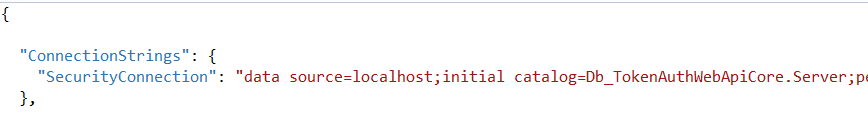
Create an AppSettings.json file and add a ConnectionString: SecurityConnection
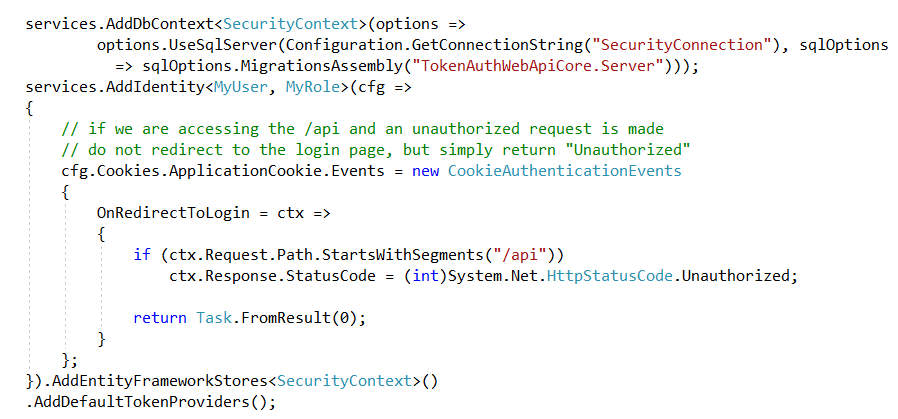
Open StartUp.cs class , locate ConfigureServices method : ConfigureServices(IServiceCollection services) and add the following to configure our SecurityContext to point to SecurityConnection witch point to sql database configured in AppSettings.json file
Configure Asp.Net Core Indentity to use our custom user and role ( MyUser and MyRole)
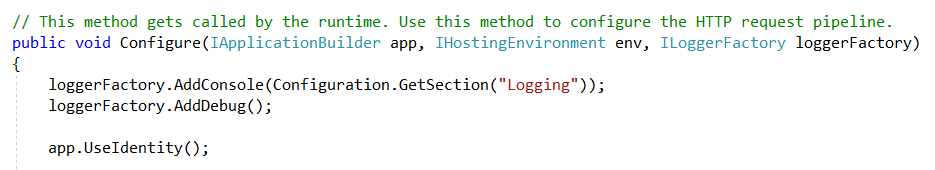
Locate Configure method and add app.UseIdentity in middleware
Open Package Manager Console.
Initialise migration : add-migration init
Upadate or Create the Database : update-database
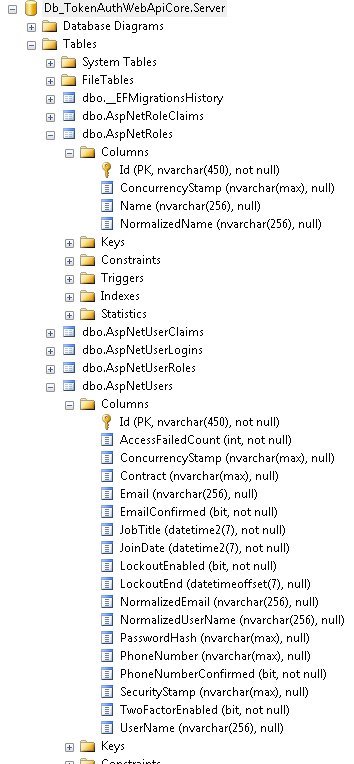
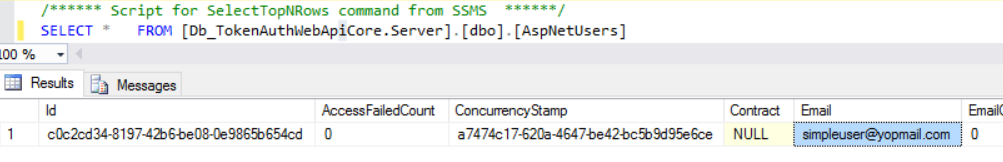
The generated database looks like this
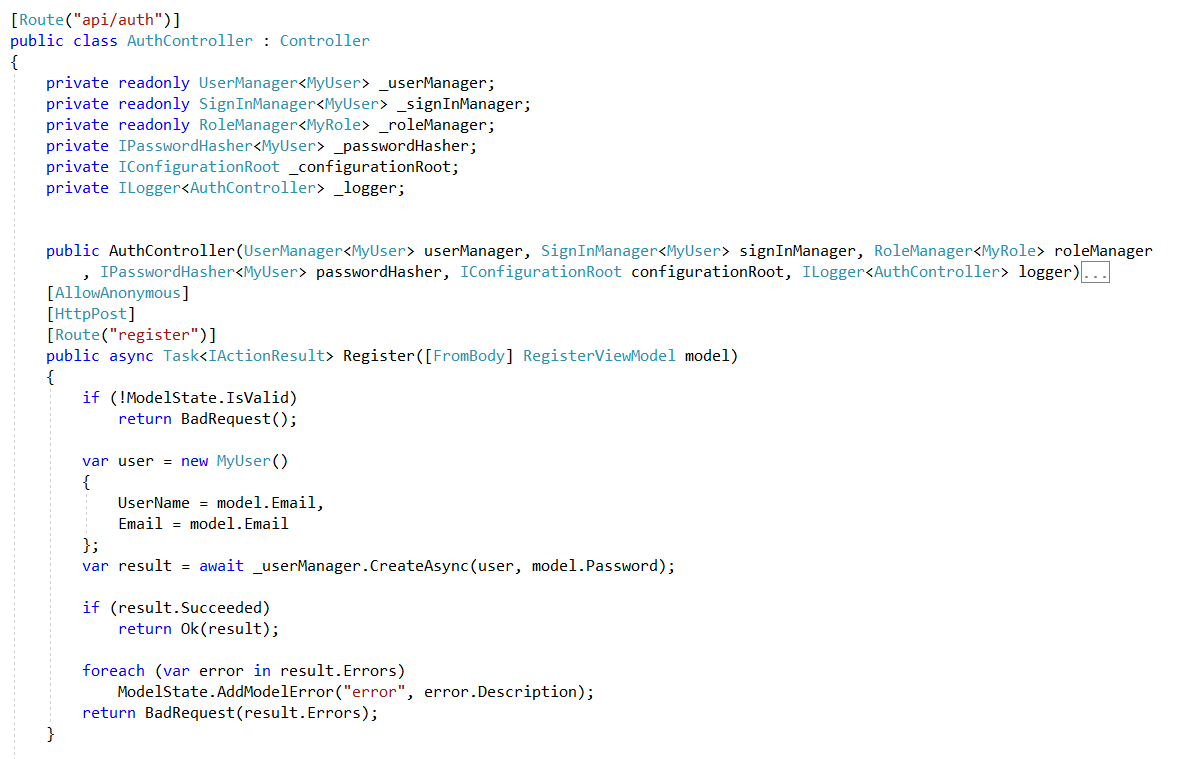
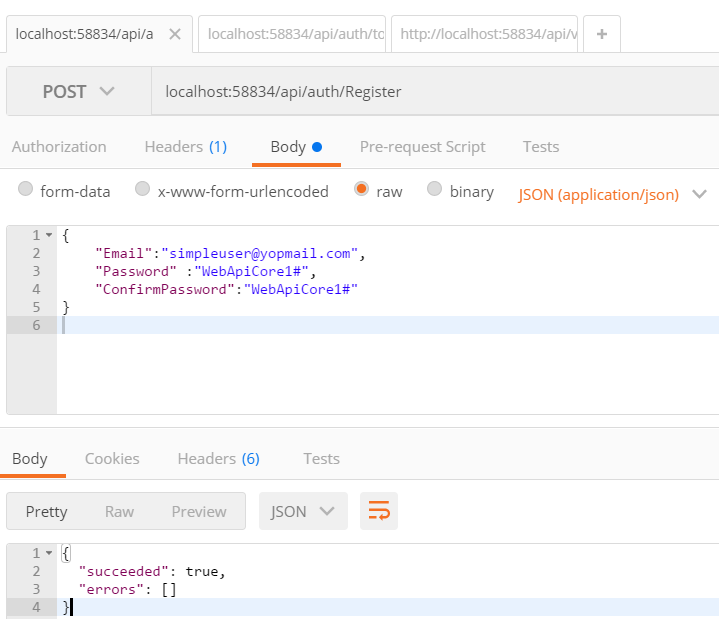
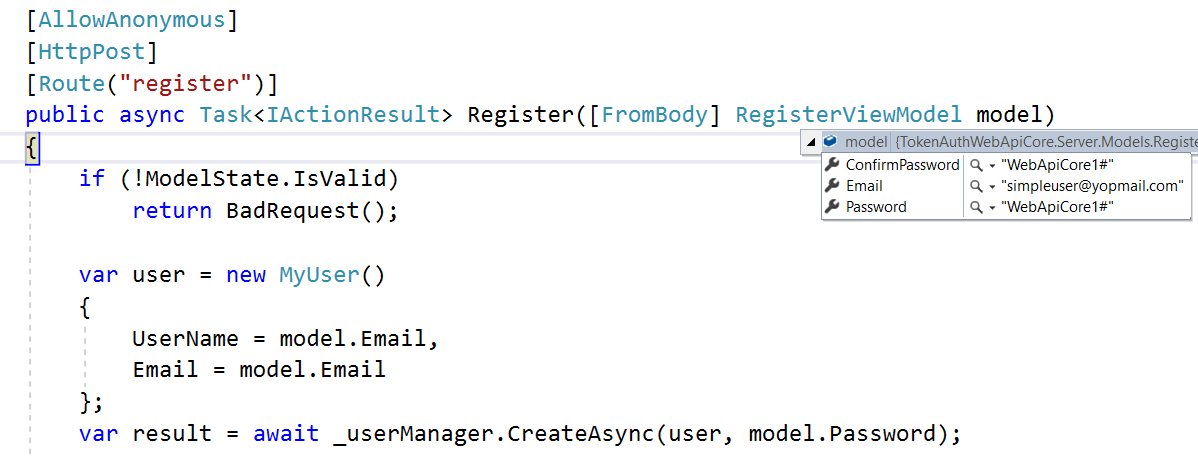
Register User
Test Register user
I use a google extensions Postman to test api
Get Ressources
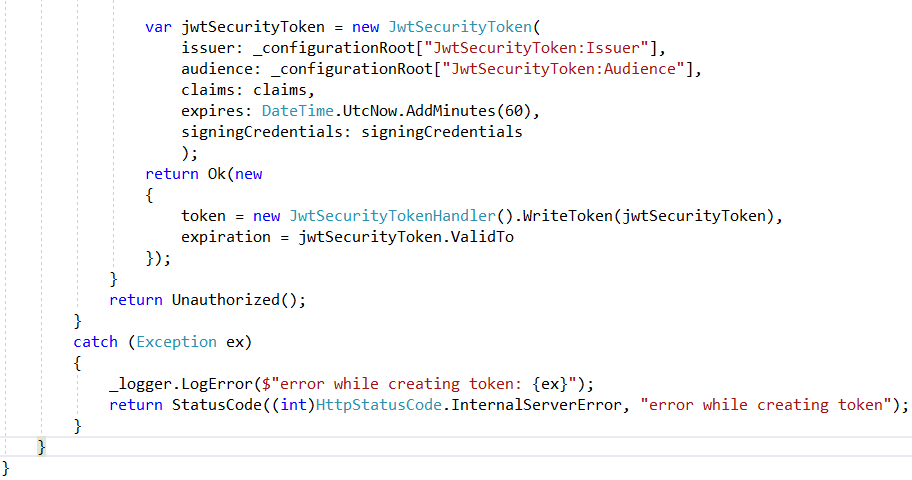
Here , I log the user , if the user is authenticated with its credentials (email and password), I get the user claims , add additionnal claims related to JWT, Create Security Token and return it
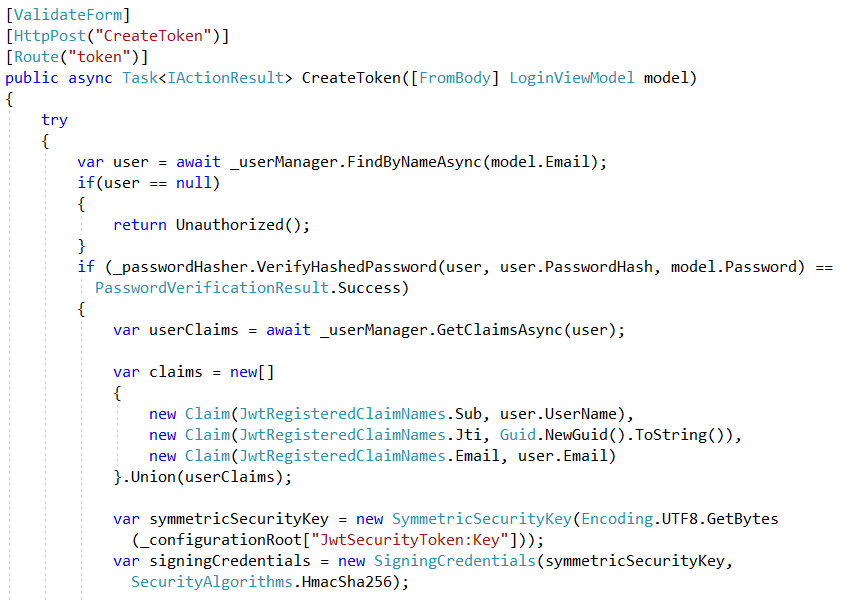
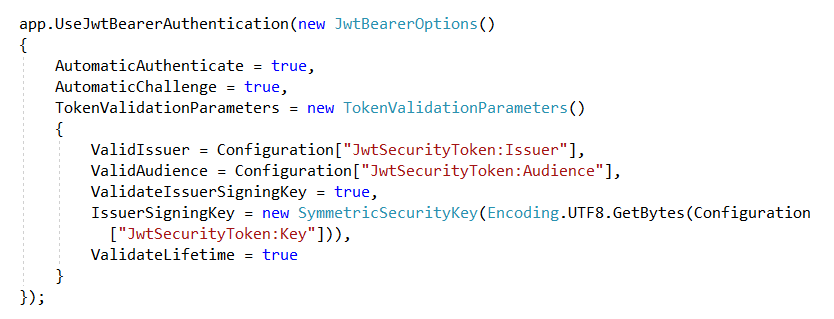
Locate Configure method and app.UseJwtBearerAuthentication in middleware to validate the token
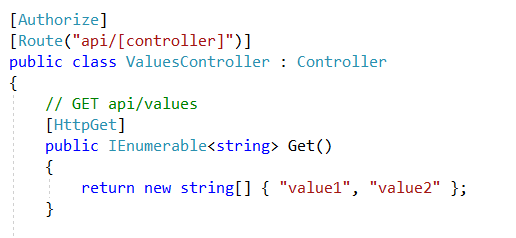
The protected ressource look like this
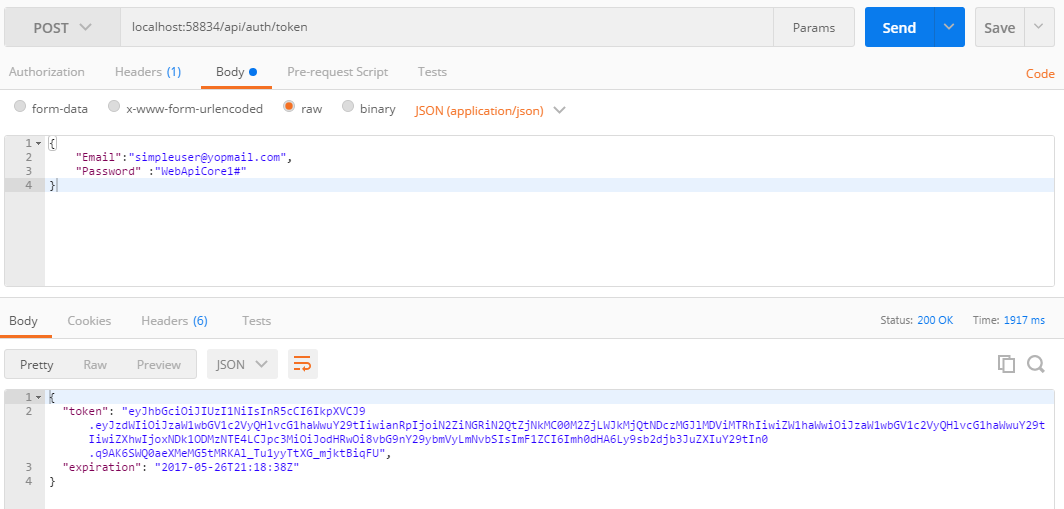
Test API With Postman
get token (localhost:58834/api/auth/token)
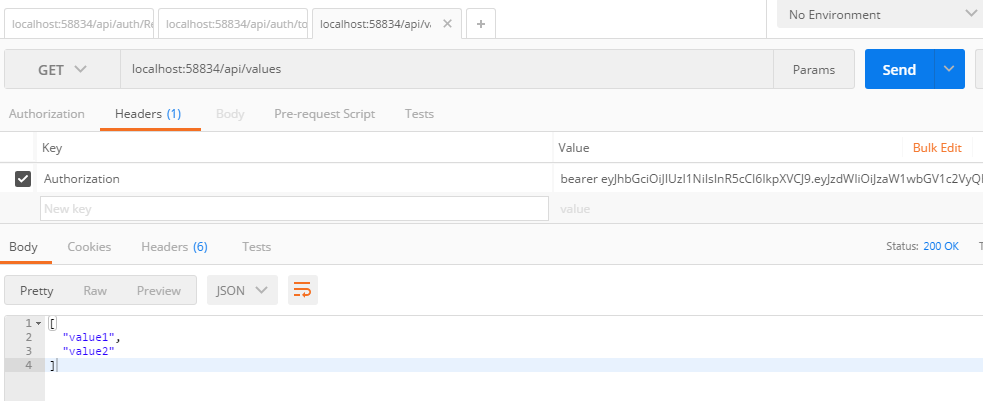
Send Query to get ressource by including valid token in the header (localhost:58834/api/values)
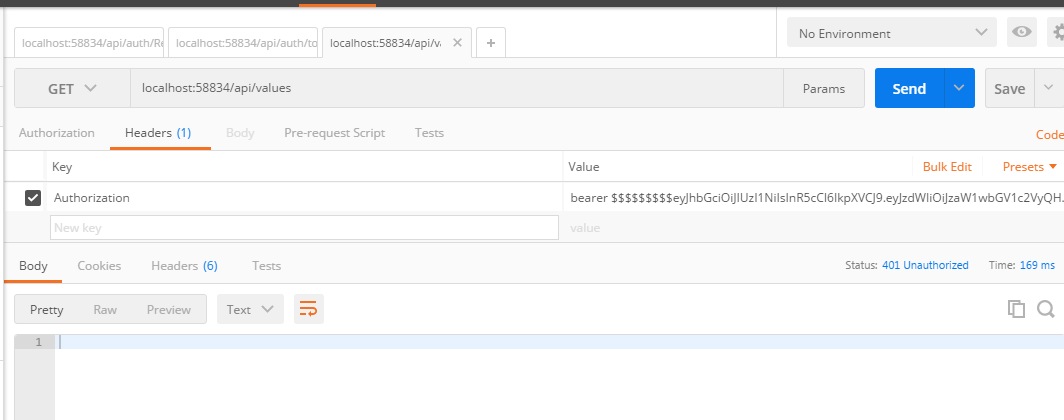
Send Query to get ressource by including invalid token in the header (localhost:58834/api/values)
The entire scenario
Code source is available on my Github repository (https://github.com/logcorner/token-based-authentification-using-asp.net-web-api-core)
Best regards