Building micro services through Event Driven Architecture part18 : Securing Query HTTP API using Azure Active Directory B2C
Building micro services through Event Driven Architecture part18 : Securing Query HTTP API using Azure Active Directory B2C
This tutorial is the 18th part of a series : Building microservices through Event Driven Architecture.
The previous step is about Building micro services through Event Driven Architecture part17 : Securing Command HTTP API using Azure Active Directory B2C.
If you have followed the previous tutorial , you can skip this one or use it as an exercice because the process is identical
In this tutorial, I will show how to use an identity provider to secure the query http api microservice by enabling Oauth2 and OpenId Connect using Azure AD B2C.
Azure Active Directory B2C provides business-to-customer identity as a service. Your customers use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.
Learn more about Azure AD B2C in What is Azure Active Directory B2C?
Azure Active Directory B2C
To setup Azure AD B2C as an identity provider , I need to create a B2C tenant wich is different from a Azure AD tenant
Azure AD B2C is a separate service from Azure Active Directory (Azure AD). It is built on the same technology as Azure AD but for a different purpose – to allow businesses build customer facing application and then allow anyone to sign up into those applications with no restrictions on user account.
Learn more about Azure AD in What is Azure Active Directory?
Securing Query HTTP API
To protect the query HTTP API microservice, I need to register an application in the azure AD B2C tenant, expose the API, define scopes , configure the web api to use Azure AD authentication and finally enable SwaggerSecurityDefinition
Azure AD B2C Application Registration
Go to the tenant and click app registration and fill in the form accordingly : provide an application name, the supported account types. Here I do not need a redirect URI because it is a web api.
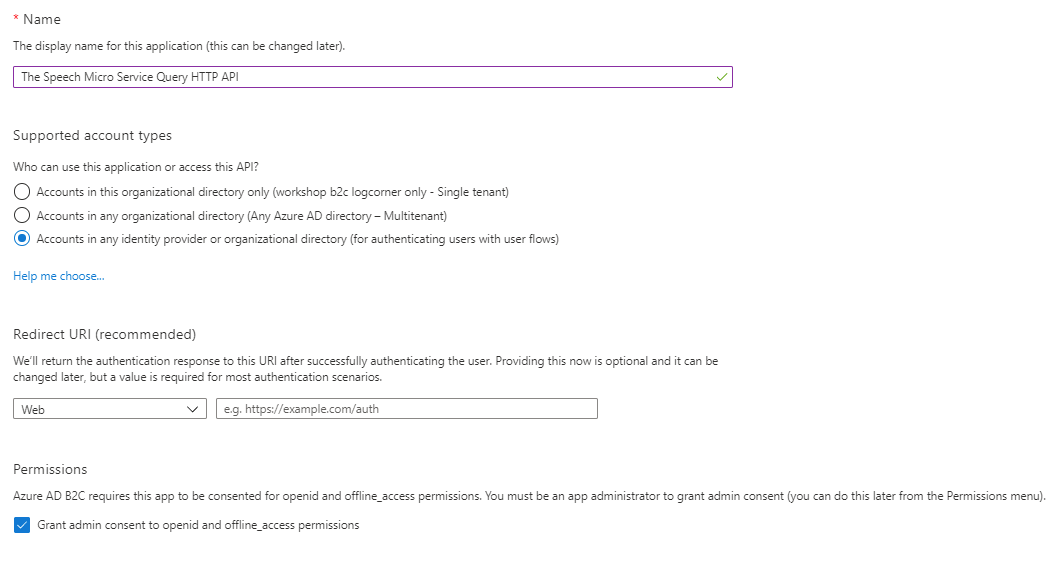
Click on Expose an api and set the application ID URI (in my case https://workshopb2clogcorner.onmicrosoft.com/query/api)
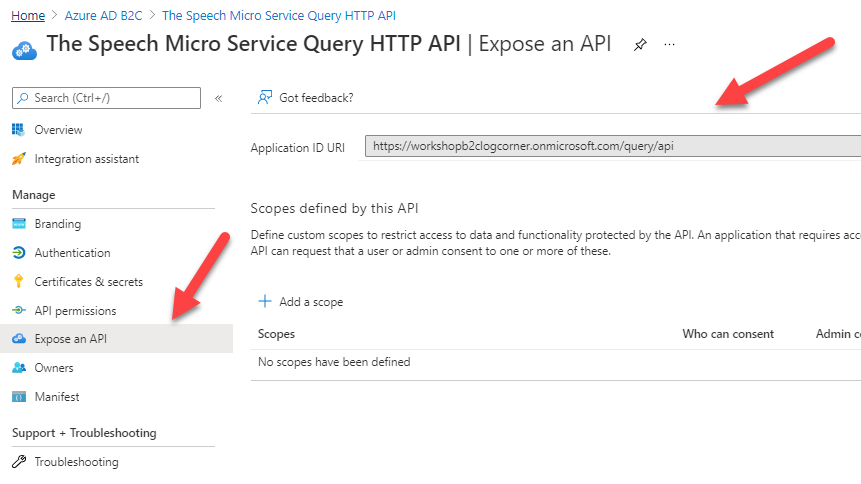
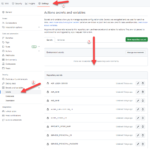
Add the API scope Speech.List to enable users to grant consent. users should consent these scope to be allowed to list the speeches.
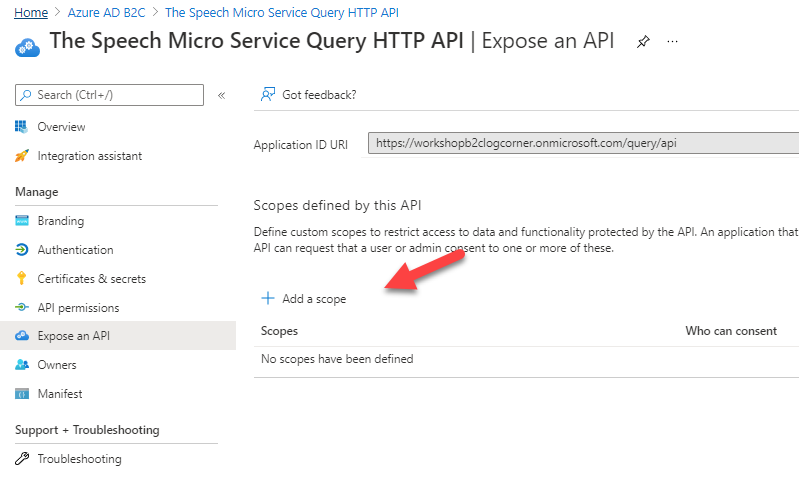
So click on Add a scope and provide the scope name , display name and description
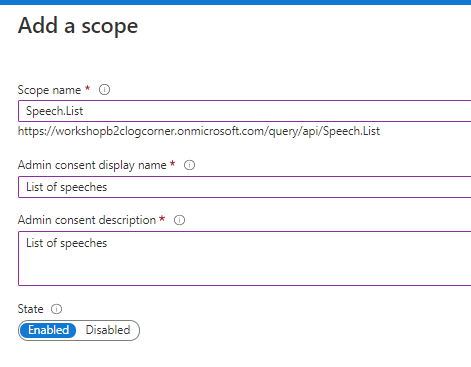
Configure Query HTTP API
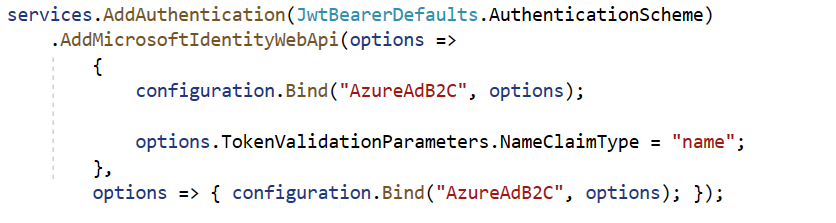
Open the startup.cs class and add the following to register services required by authentication services and protects the web API with Microsoft identity platform
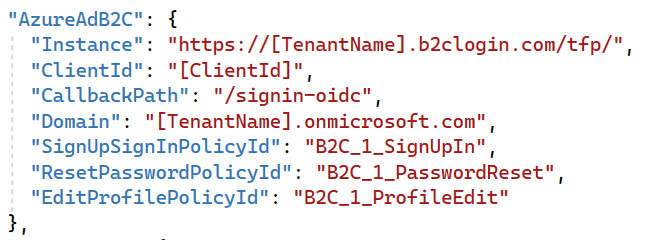
Open appsettings.Development.json and add the folllowing
Replace [ClientID] with the identifier of the application you registered ealier and [TenantName] with the name of your tenant in my case workshopb2clogcorner.
Registers services required by authentication services and protects the web API with Microsoft identity platform
The user flows B2C_1_SignUpIn, B2C_1_PasswordReset and B2C_1_ProfileEdit was configured in the step 16 Building micro services through Event Driven Architecture part16 : Azure Active Directory B2C : https://logcorner.com/building-micro-services-through-event-driven-architecture-part16-azure-active-directory-b2c/
OpenAPI Specification : Enable Swagger
To test , document and use the api in real life , I’m going to use the open api swagger specification. for more information about swagger, I siggest you to follow this link https://swagger.io/resources/open-api/.
I have first to register the swagger web appliction in azure AD B2C tenant. just open your azure AD tenant , click on app registration as you did in the previous step : provide a name, the account types and the redirect uri should be http://localhost:7000/swagger/oauth2-redirect.html where http://localhost:7000 is the host of the web api.
Because after the authentication process , you should be redirected back to the swagger UI.
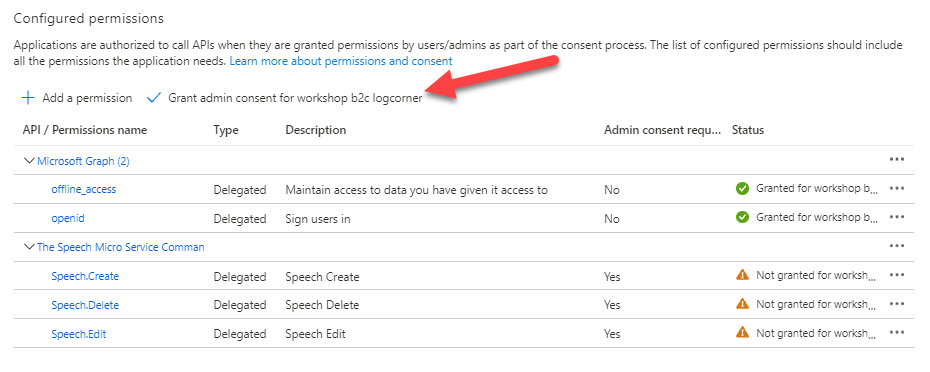
To authorize the swagger UI to call the web api, I should grant the admin consent for the tenant.
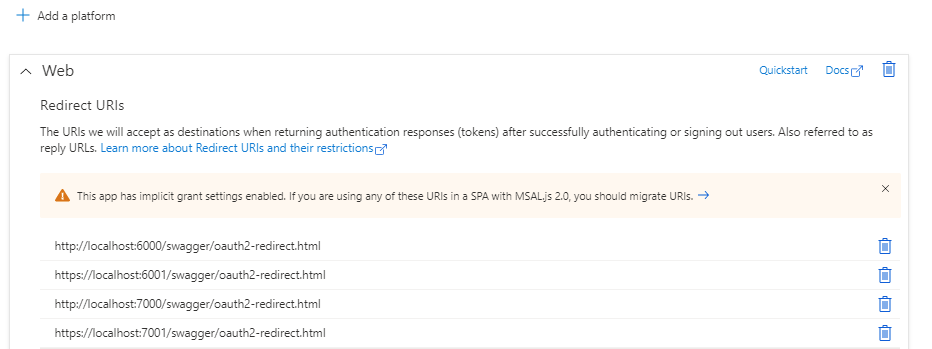
So open the swagger UI app registration and click on API Permissions
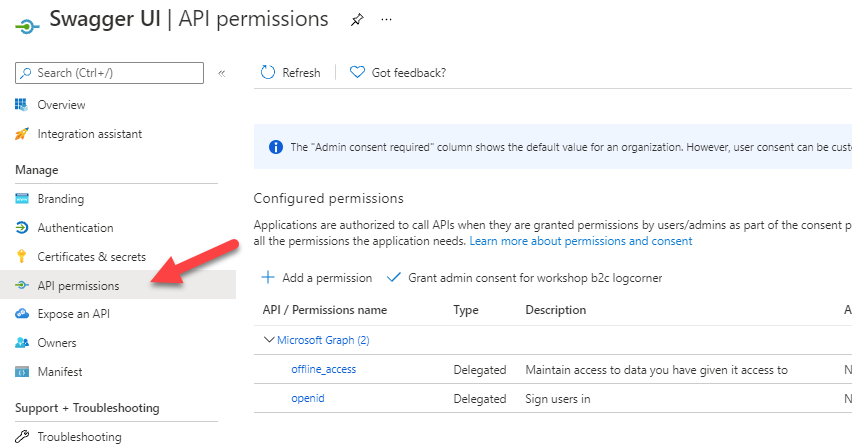
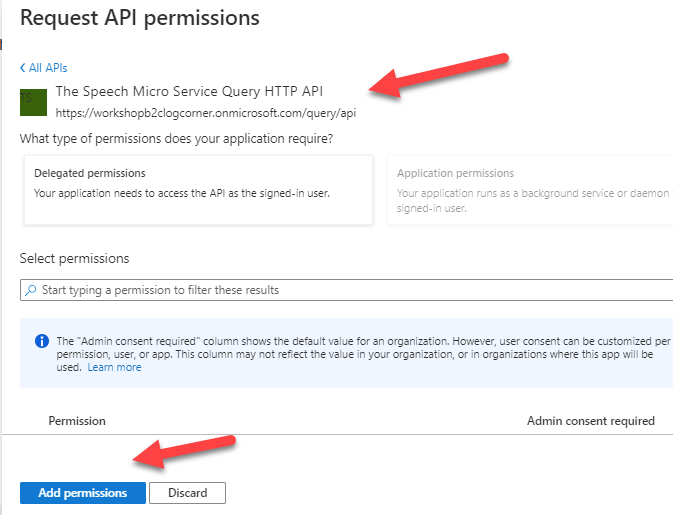
Click on Add a permission button and select My APis and choose the web API you registered earlier.
Select all the scopes and click on Add Permissions
Finally click on click grant admin consent for {your tenant}
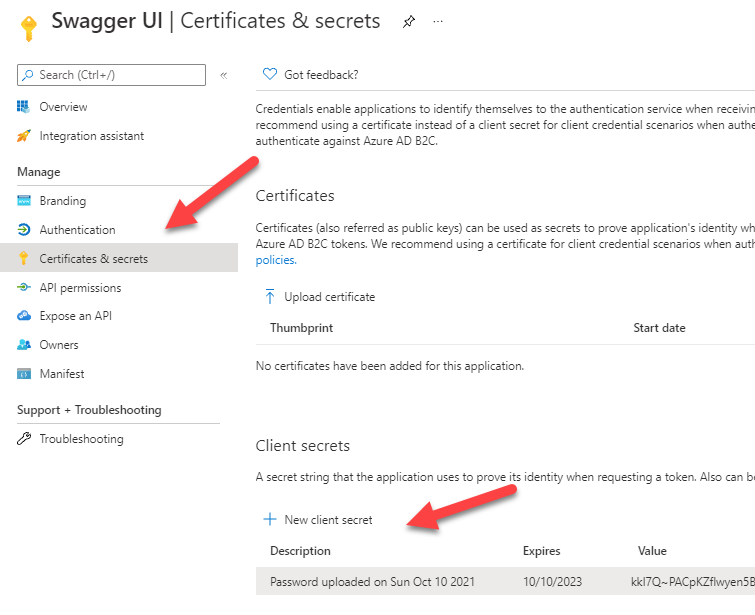
Click on Certificates & secrets and create a new client secret. you should keep it for use later because you cannot see it again.
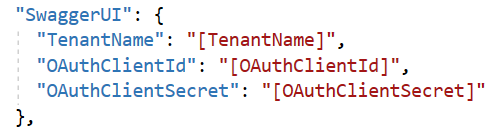
Open appsettings.Development.json file add the swaggerUI section where :
[TenantName] is the name of your B2C tenant
[OAuthClientId] is the swaggerUI application identifier you registered.
[OAuthClientSecret] is the client secret you created
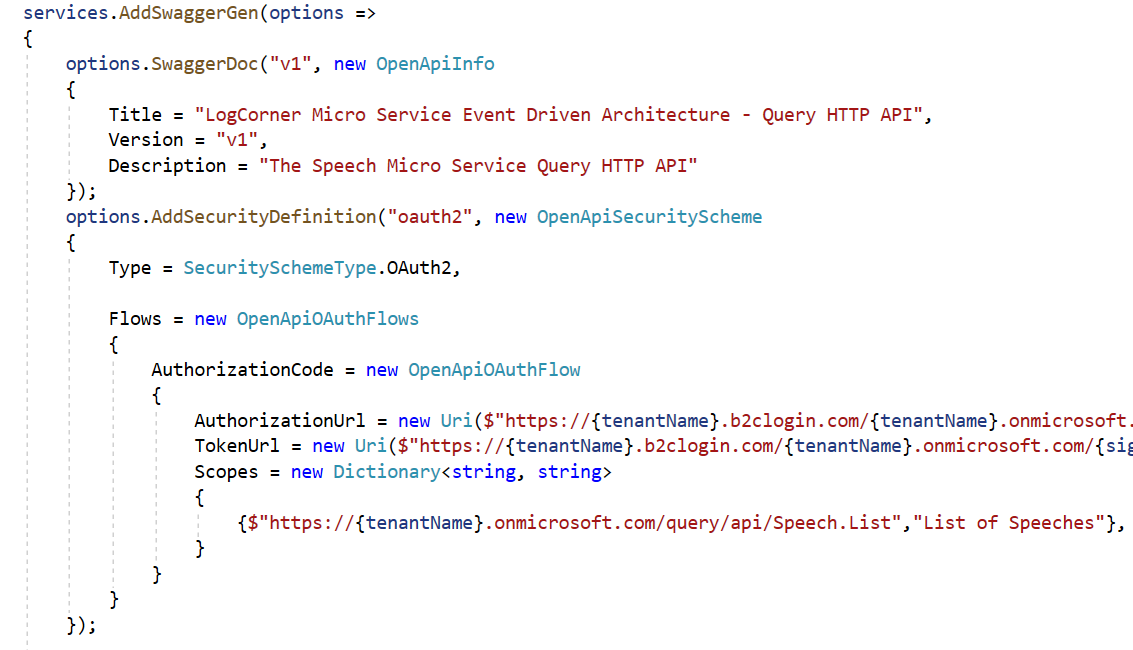
Open startup.cs class and the following code
options.AddSecurityDefinition
Add a securityDefinition to describe how your API is protected to the generated Swagger
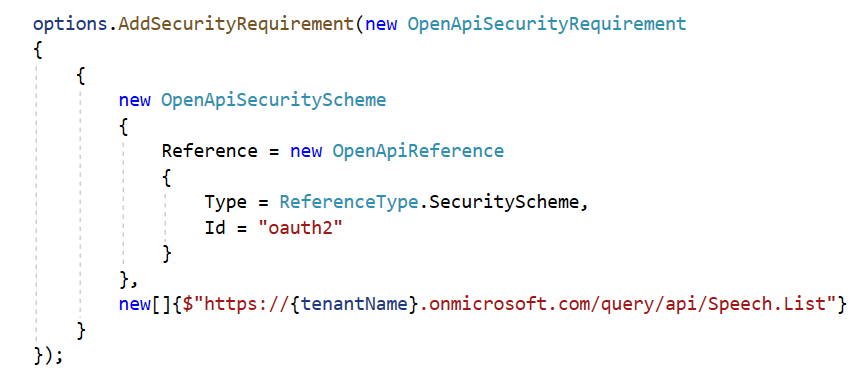
options.AddSecurityRequirement
Add a global security requirement. Here you should add the list of scopes and OpenApiReference to oauth2.
Testing
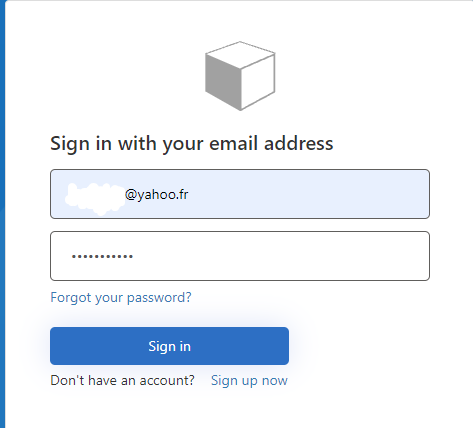
Run the application and navigate to ttp://localhost:7000/swagger/index.html or https://localhost:7001/swagger/index.html and click on Authorize button
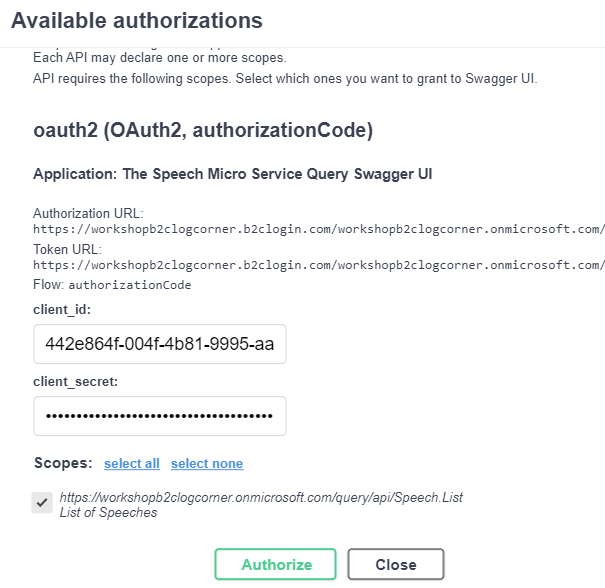
Enter the user credentials ( should be a user of the tenant)
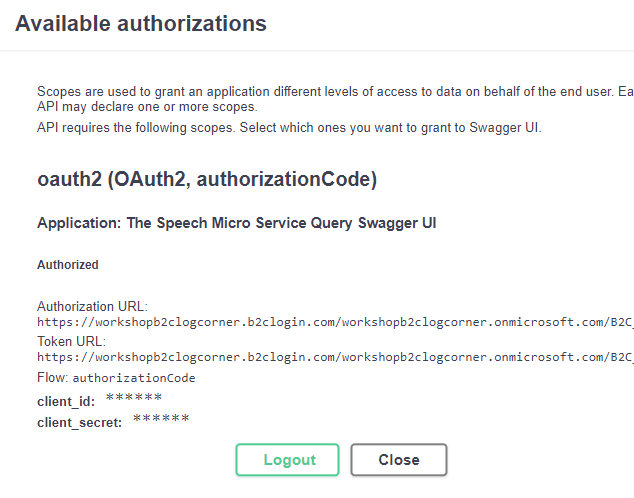
Click on Close
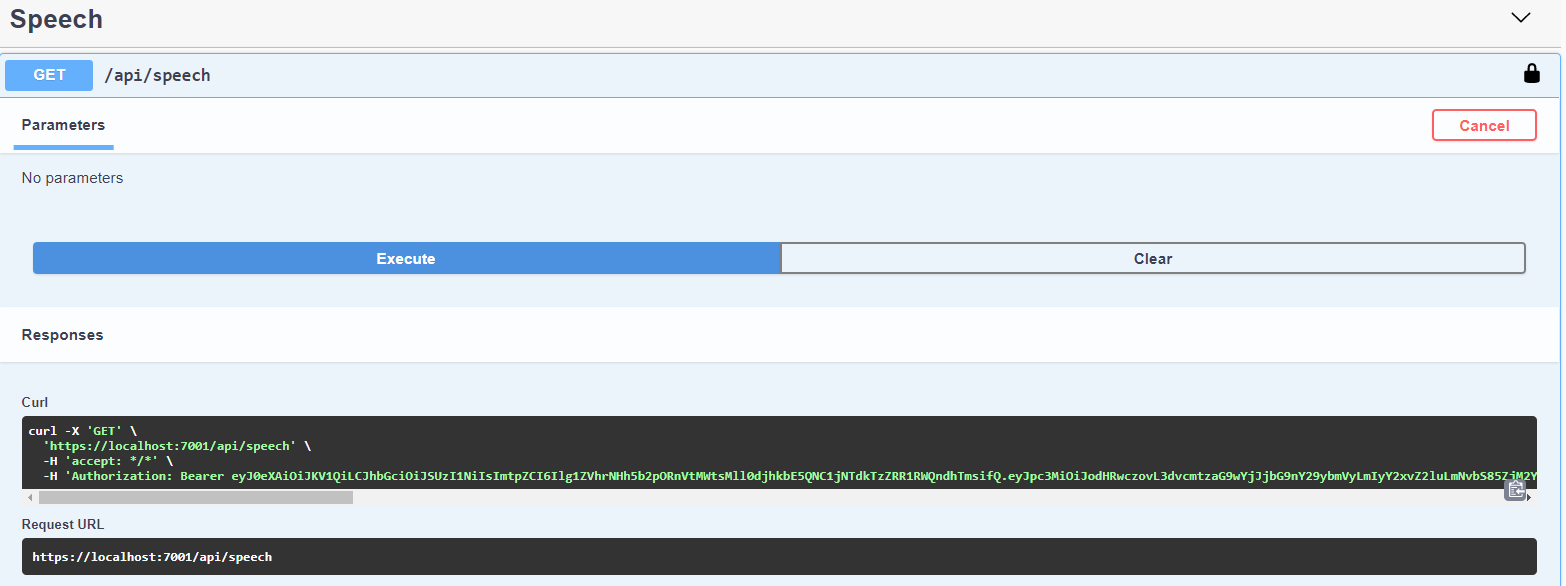
You will be able to call the api
Code source is available here :
Thanks for reading, if you have any feedback, feel free to post it
Regards